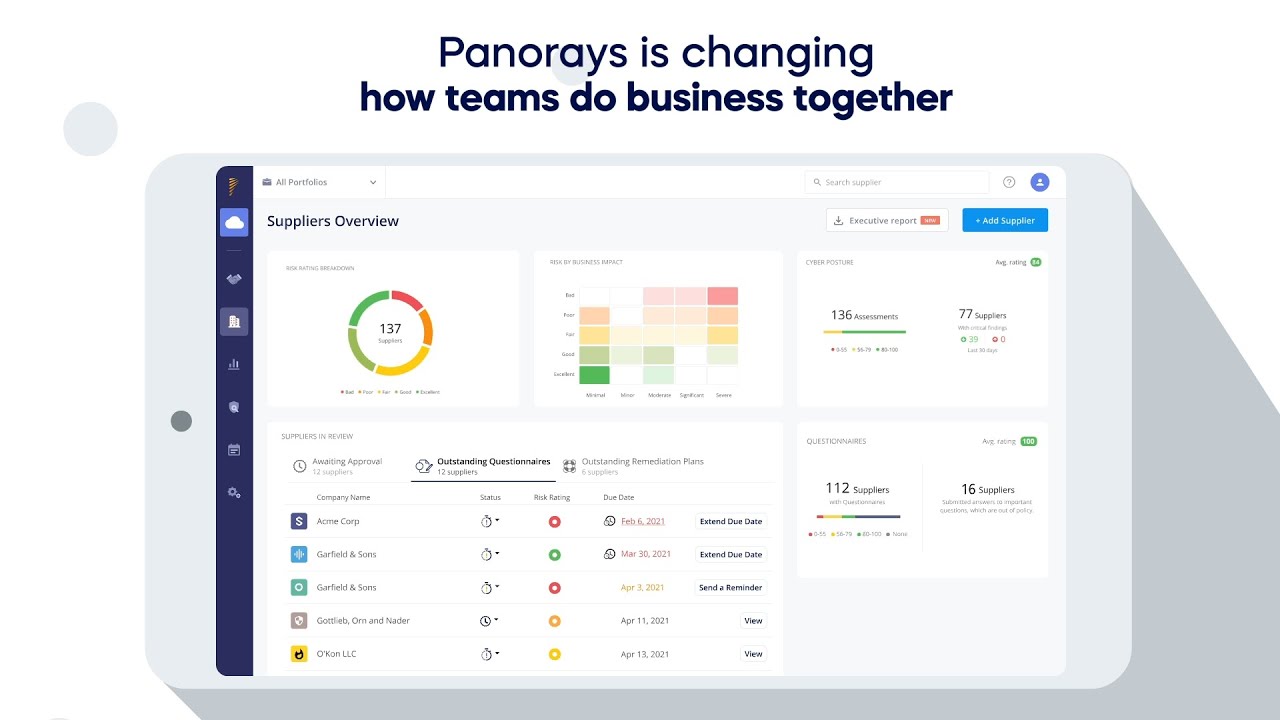
See Panorays in Action
Speak to one of our experts and learn how Panorays lets you manage third-party cyber risks from one automated platform.
By clicking submit, I consent to the use of my personal data in accordance with Panorays Privacy Policy.
Get a customized one-on-one demo and learn how to:
- Evaluate third party risks with an integrated view of security questionnaires and external cyber assessments.
- Collaborate with third parties to quickly remediate security gaps.
- Monitor and respond to third-party risks with real-time alerts on changes to risk levels and emerging cyber threats.