Third-Party Cyber Risk Management
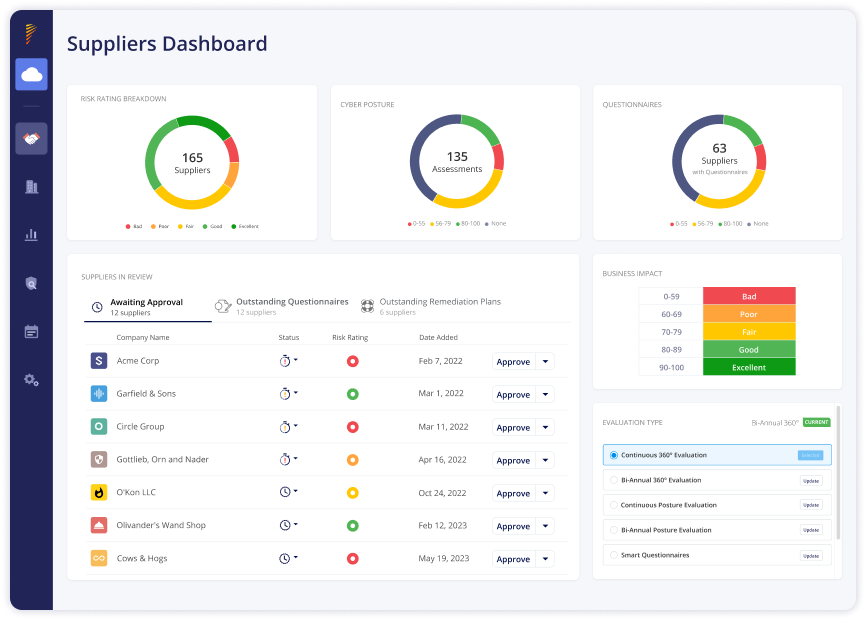
Onboarding at Scale
Panorays streamlines the onboarding process by detecting hidden Nth parties along your supply chain, and automating the collection and verification of third-party documentation and assets. Within hours, Panorays makes it easy to detect, track, and assess hundreds of third parties at scale, while prioritizing them based on their criticality and business impact.
Comprehensive Risk Assessments
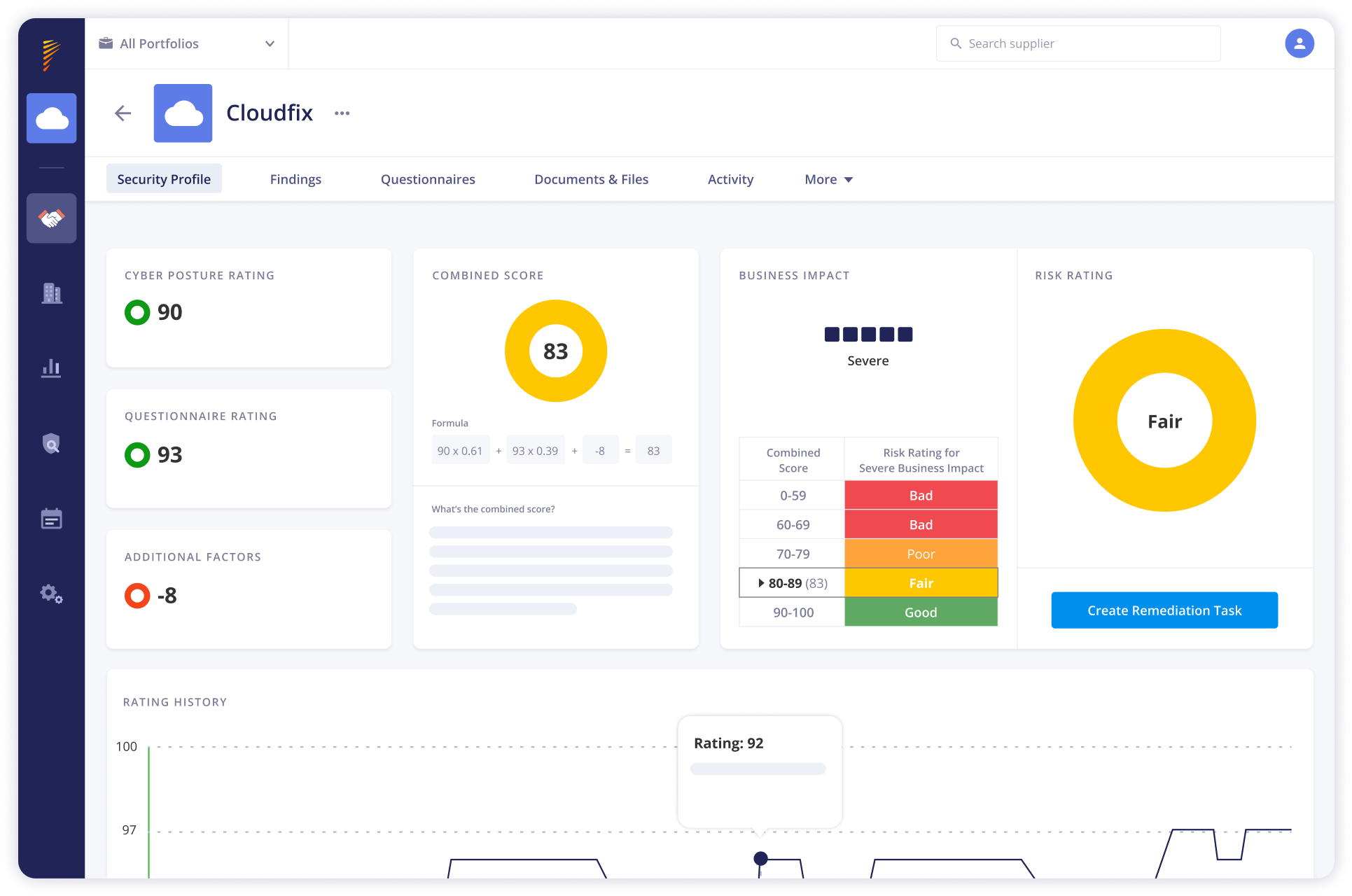
Panorays conducts detailed third-party risk assessments by analyzing cybersecurity posture against industry standards and regulations, providing detailed risk ratings and actionable insights to prioritize remediation efforts and manage threats across your supply chain.
Continuous Monitoring and Threat Detection
Continuously monitor changes in third-party security posture in real-time, leveraging automated alerts and threat intelligence to identify potential risks or vulnerabilities before they materialize.
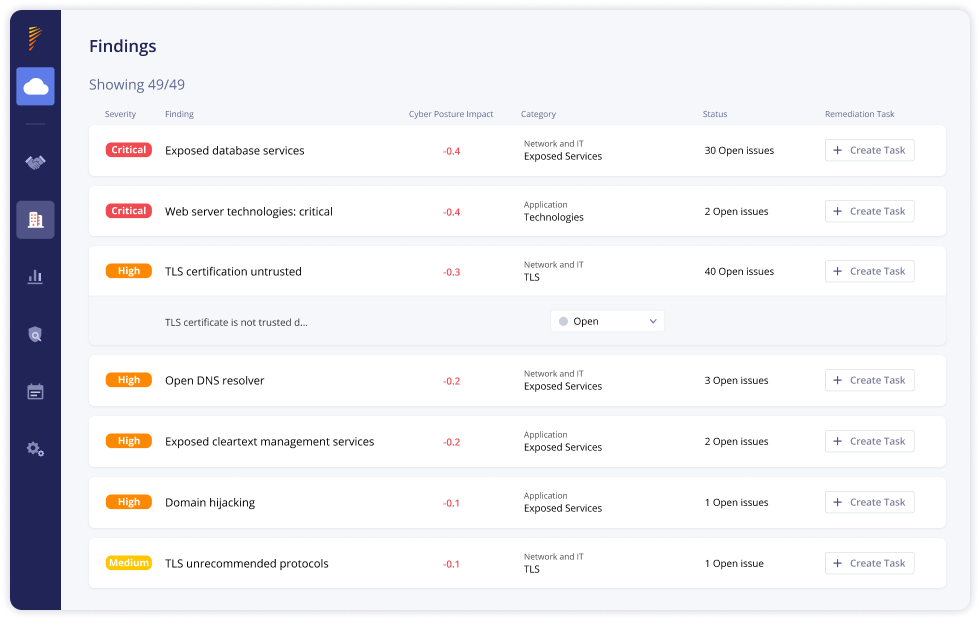
Effortless Remediation and Collaboration
With auto-generated remediation plans, Panorays allows you to prioritize threats and work together with vendors to close security gaps. With centralized communication, documentation sharing, and progress tracking, Panorays ensures transparency and accountability throughout the vendor lifecycle.
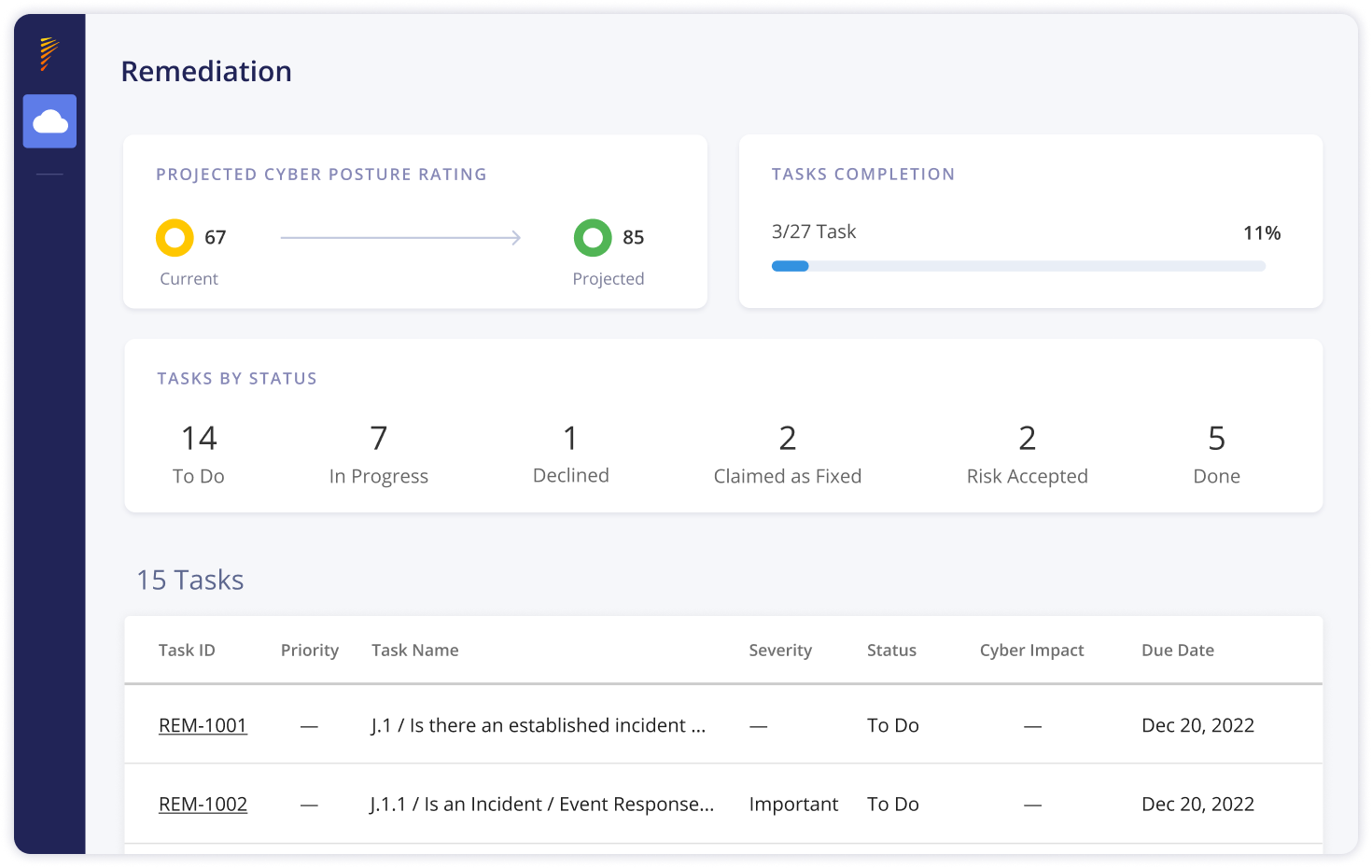
Reduce Exposure Along Your Supply Chain
See Your Risks In Context
Secure Your Entire Attack Surface

Remediate Security Gaps in Minutes
Prioritized, Context-Based Third-Party Risk Management
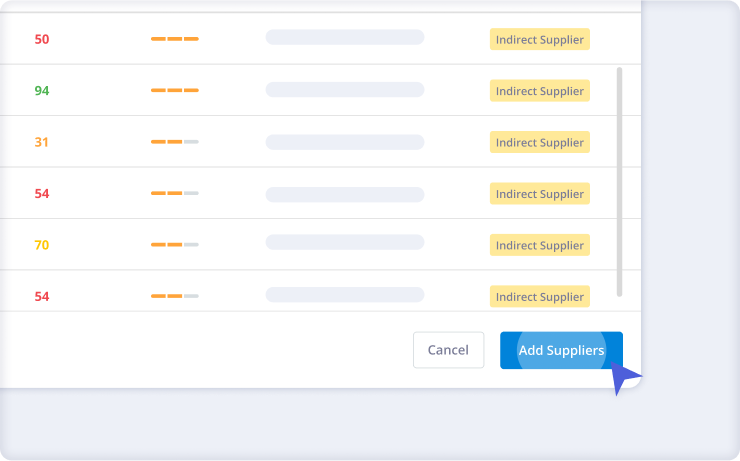
Identify Supply Chain Risks
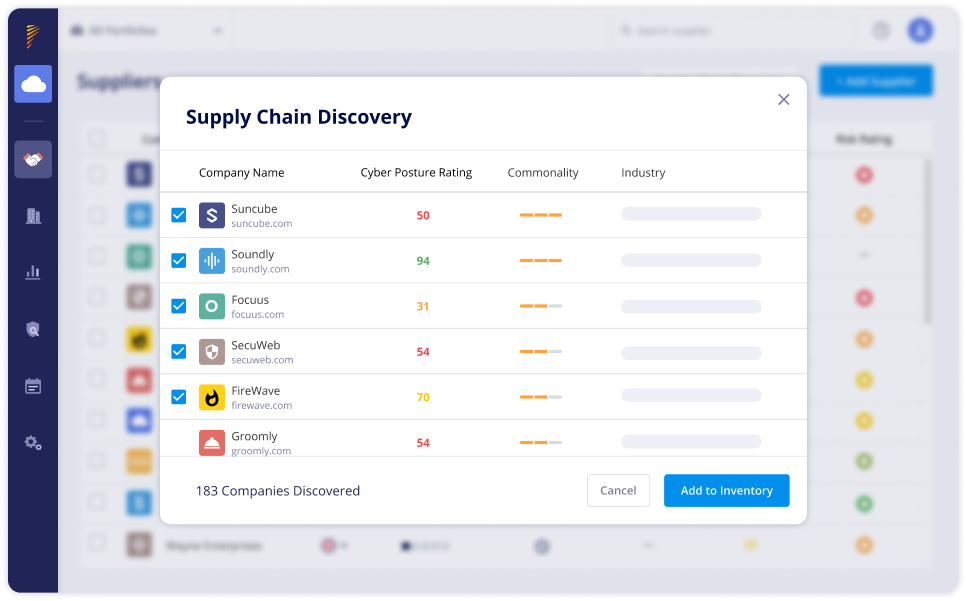
Panorays’ enhanced Supply Chain Detection discovers 3rd-Nth parties along your supply chain, uncovering hidden risks and exposing Shadow IT. Review hundreds of vendors and add the most critical ones for close monitoring and assessment.
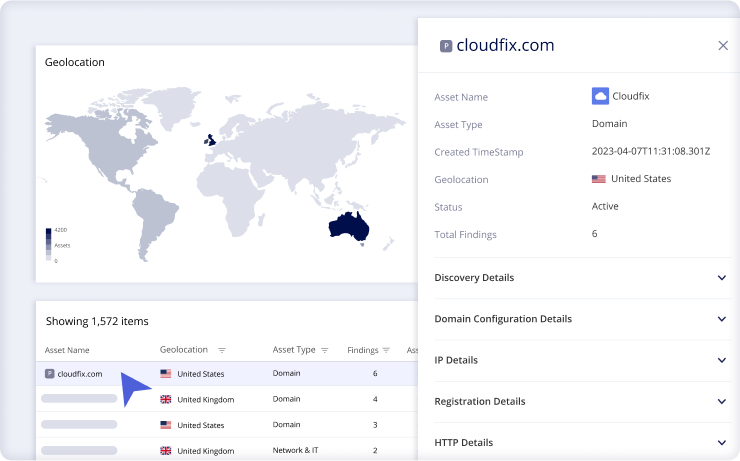
Gain Visibility Into Third-Party Risk
Our Risk DNA Assessments collect and analyze third-party cyber risks, enabling organizations to understand their risk profiles and prioritize mitigation efforts effectively. Panorays provides contextual insights and risk ratings, empowering businesses to make informed decisions and strengthen their security posture against evolving threats.
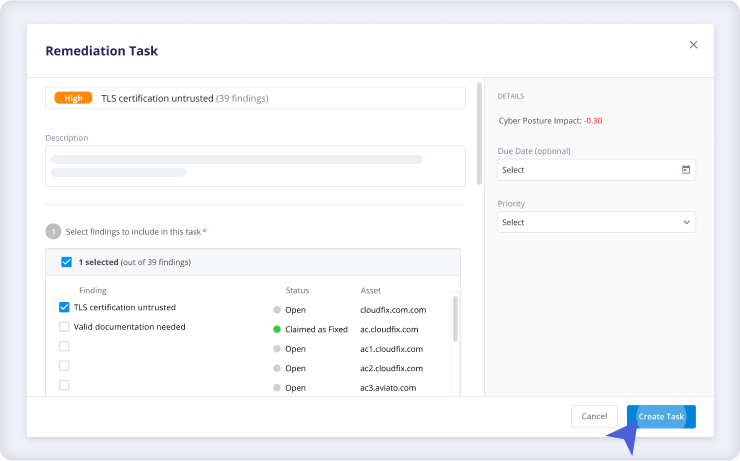
Close Security Gaps
Panorays allows for effortless remediation by providing actionable recommendations based on identified risks and compliance requirements. With integrated workflow tools and collaboration features, organizations can efficiently track and manage remediation tasks, accelerating the resolution process and reducing exposure to potential threats.
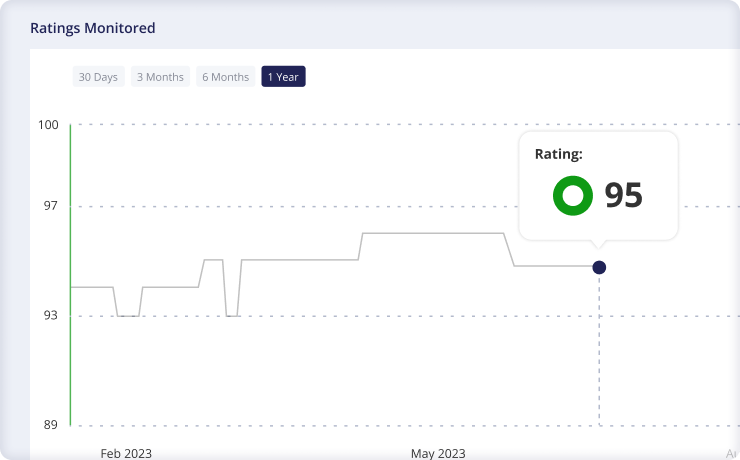
Stay Ahead of Threats
Continuously monitor third parties with real-time visibility into their evolving cyber risks. With automated assessments and alerts, Panorays enables organizations to stay ahead of emerging threats, adapt their risk management strategies dynamically, and maintain adaptive cybersecurity defenses across their supply chain ecosystem.
-

Identify Supply Chain Risks
Panorays’ enhanced Supply Chain Detection discovers 3rd-Nth parties along your supply chain, uncovering hidden risks and exposing Shadow IT. Review hundreds of vendors and add the most critical ones for close monitoring and assessment.
-

Gain Visibility Into Third-Party Risk
Our Risk DNA Assessments collect and analyze third-party cyber risks, enabling organizations to understand their risk profiles and prioritize mitigation efforts effectively. Panorays provides contextual insights and risk ratings, empowering businesses to make informed decisions and strengthen their security posture against evolving threats.
-

Close Security Gaps
Panorays allows for effortless remediation by providing actionable recommendations based on identified risks and compliance requirements. With integrated workflow tools and collaboration features, organizations can efficiently track and manage remediation tasks, accelerating the resolution process and reducing exposure to potential threats.
-

Stay Ahead of Threats
Continuously monitor third parties with real-time visibility into their evolving cyber risks. With automated assessments and alerts, Panorays enables organizations to stay ahead of emerging threats, adapt their risk management strategies dynamically, and maintain adaptive cybersecurity defenses across their supply chain ecosystem.
The Essentials You Need for Comprehensive
Third-Party Cyber Risk Management

Attack Surface Monitoring
Supply Chain Discovery
Vendor Lifecycle Management
Incident Response Portal

Consolidated Risk Assessments

In-Platform Communication
Frequently Asked Questions
-
Third-party cyber risk management involves identifying, assessing, and remediating potential cybersecurity threats and vulnerabilities posed by external entities such as vendors, suppliers, or partners that are a part of an organization’s digital landscape.
-
Third-party cyber risk management is crucial because it helps organizations protect themselves from security breaches, data leaks, and other cyber threats that could originate from their relationships with external parties, safeguarding sensitive information and preserving trust with customers and stakeholders.
-
The degree of third-party cyber risk management needed varies depending on factors such as the sensitivity of the data shared with external parties, the potential impact of a security breach, and the regulatory requirements applicable to the organization’s industry. A thorough risk assessment can help determine the appropriate level of management needed.
-
When selecting a third-party cyber risk management framework, consider factors such as its alignment with industry standards, the comprehensiveness of its risk assessment methodologies, its scalability to accommodate the organization’s needs, and its ability to facilitate ongoing monitoring and mitigation of cyber risks posed by external entities. Additionally, assess its compatibility with existing cybersecurity practices and technologies within the organization.
Manage Third-Party Cyber Risks With Ease
See How Panorays Supports Supply Chain Cyber Risk Management
Hundreds of teams evaluate and manage their vendors’ security with Panorays